Ransomware Group Claims Responsibility for Attacks Exploiting Flaw in File Transfer Software MOVEit; more than 100 companies have already been victimized
More than 100 major companies around the world, including the BBC, British Airways and Zellis, have already fallen victim to a wave of attacks that exploit security holes to break into internal systems and steal confidential data. The scams started last week and caught the attention of the UK and US governments, among others, who focused attention on the vulnerability in the MOVEit file transfer software.
- Old, unpatched vulnerabilities are the biggest threat to businesses
- With so many advances in security, why do cyberattacks keep happening?
The solution, from vendor Progress Software, focuses on data management with the addition of encryption, analytics and automation tools. It was also there that the vulnerability tracked as CVE-2023-34362 was found, already fixed by the developers, but which has been used in attacks against vulnerable infrastructures around the world – at least six of these allegedly belong to large Brazilian companies.
The gang known as Cl0p, but also carrying names such as TA505, FIN11 and Lace Tempest, which define the central operation or its affiliates, are allegedly behind the attacks. Cybercriminals specialize in ransomware scamsbut in the case of MOVEit, they use the zero-day vulnerabilitythat were unknown even to the original developers, to invade servers and steal sensitive data from affected companies.
The blows are painful. The British media network BBC, for example, has informed officials that documents, home addresses, identification numbers and dates of birth have been stolen by criminals. At British Airways, in addition to personal data, the financial information of workers was also compromised, while the Canadian province of Nova Scotia was the first government target to come forward claiming to have suffered an attack.
Meanwhile, the cybercriminals are speaking directly to the press, revealing that the stolen information will be compiled on an obscure website, with affected companies receiving ransom demands for undisclosed amounts so as to keep the data confidential. If not, they will be published, in a common extortion tactic similar to ransomware attacks, which in any case proves to be very effective and profitable.
“Groups have moved away from file encryption, which is common in data hijacking attacks, and have focused solely on information theft,” explains Satnam Narang, a research engineer at cybersecurity firm Tenable. The expert defines the current scenario as “emerging” and underlines the urgency of applying updates for companies to protect themselves.
The bug has been fixed, but the attacks continue

As with other major vulnerabilities in recent years, such as Log4J, we are talking about a security breach whose fix has been available since the last week. While cybercriminals say they started their offensive wave on May 29, an update for MOVEIt was released on June 1, but the opening continues to spawn attacks worldwide.
The US Government Infrastructure and Cybersecurity Agency (CISA) has ordered all government agencies to update their MOVEIt solutions within the next 15 days. Similar warnings have also been issued by organizations in the UK and the European Union, while Cl0p operators have teased, saying data obtained from government, hospital and military branches will be wiped from their systems.
The date chosen by the bandits, by the way, was no coincidence. It is Memorial Day, a major national holiday in the United States, when citizens honor fallen soldiers. It is also a time when there are fewer specialists active in digital security departments, which in itself causes a delay in incident response.
More than a week later, however, the problems persist. According to OpenCTI.BR data, more than two thousand MOVEIt servers were still vulnerable to exploitation this Tuesday morning (6). As mentioned, six of them are located in Brazil, entitled to the infrastructure of large national companies, including a large insurance company.
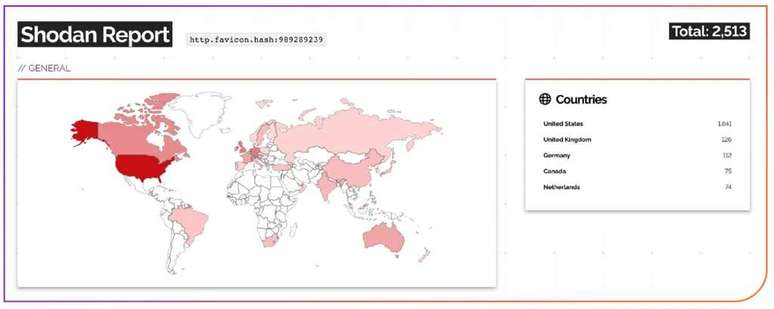
However, simply applying the fix does not solve the problem. “Because the attacks started before an update was available, companies should check for signs of a compromise beyond those publicly discussed. The patch will not remove the malware and other artifacts of the breach, so an analysis of the compromise is critical” , explains Christopher Budd, Senior Manager Threat Research at Sophos.
Tenable CEO Amit Yoran goes further, indicating that the wave of attacks involving MOVEIt should serve as a warning sign for companies to commit to keeping systems updated, but also monitored. Such a check could have prevented the worst, while using systems to understand the attack surface would have meant more preparation for a bomb seen as inevitable.
“Vulnerabilities are being disclosed every day, with threat actors just waiting to see if they can be monetized. Rather than waiting to be attacked before responding, it’s critical that security teams take a proactive approach.” Yoran joins the chorus: we are only at the beginning of the wave, with other organizations coming forward in the coming days to reveal that they have been affected.
With information from Computer that plays AND inCyber.
Trending on Canaltech:
- What is the sparkling water that accompanies coffee for?
- GM to Stop Production of Onix in June; see why
- Why do large car owners prefer not to pay IPVA? see reasons
- Robot imagines a scenario where artificial intelligence manipulates humans
- NASA Spotlight: Star-Eating Planet Astronomical Photo of the Day
- Everlasting Chemicals: Companies have been covering up health risks for decades
Source: Terra
Rose James is a Gossipify movie and series reviewer known for her in-depth analysis and unique perspective on the latest releases. With a background in film studies, she provides engaging and informative reviews, and keeps readers up to date with industry trends and emerging talents.







