Proof of concept captures radiation from power sources at close range, allowing you to acquire coded data from a distance
A new type of attack against computers and servers isolated from the Internet and conventional networks uses electromagnetic radiation as a means of data transmission. According to the proof of concept, it would be possible to acquire typed data or simple credentials from theoretically secure devices also using a common smartphone.
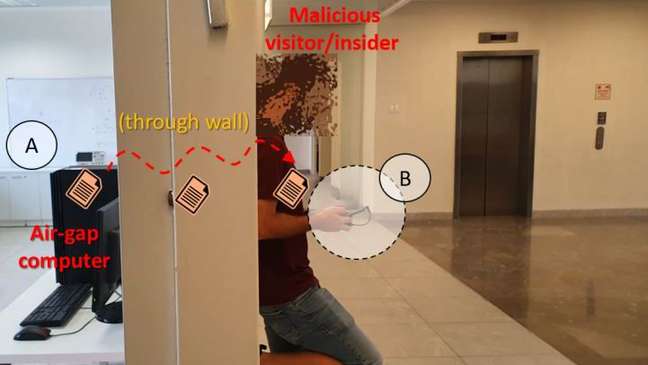
The secret lies in manipulating the frequencies of the processor during use, changing the way low-frequency electromagnetic radiation is emitted from the power supply. A malware implanted directly in the isolated machine would be enough for an antenna to pick up the signal at a short distance and, with it, the information entered by the users of these systems.
The COVID-bit exploit was presented by researcher Mordechai Guri, together with a team of experts from Ben-Gurion University of the Negev, Israel, who have already presented other attacks against isolated systems. In the first cases, the means were SATA cables And Network LEDsand in all of them the idea is to leak information in plain text, which can be used for new scams carried out later.
For the scam to work, cybercriminals need to have physical access to logged-off machines. Once a virus specifically programmed for this purpose is implanted, it begins to manipulate the CPU and other components, activating transistors that are turned off during power transmission that serve to transmit a signal that is received over short distances.
On the other side of the wall in the room where systems are limited, for example, is the attacker with a computer or smartphone, plus an antenna plugged into the headphone jack – the proof of concept even shows how the component can be disguised as such, in order not to arouse suspicion. The devices run modulators, noise reduction filters, and other wave analysis software which ultimately results in getting the transmitted information.
At the highest data rate tested, 1000 bits per second, a 4096-bit RSA encryption key could be received between four seconds and 10 minutes, while keystrokes could be logged in real time with a 20-second delay. Different devices also showed higher or lower error rates, with the cleanest signal coming from desktops and the dirtiest from notebooks, due to their power management and power management settings.
Distance also varies by device, with desktop PCs within two feet of the scanned machine still providing legible signals. Boards like the Raspberry Pi have also shown failure rates, but none of them have been able to completely invalidate the transmission performed, under ideal conditions.
Critical systems and infrastructures at risk
According to the study, the fact that the exploit requires physical access to the target device shouldn’t give peace of mind. In the crosshairs, here, are servers and computers that manage confidential data and essential systems of water, energy and other sectors, with scams involving the COVID-bit that can be carried out by highly specialized agents and in a well targeted way.
Therefore, the best way to protect yourself is to limit people’s access to these machines as much as possible and remain vigilant about threats that can come from within, from the workers who use them. Also, it’s a good idea to monitor CPU workloads and look for patterns that deviate from the norm, or lock core frequency to a certain pattern. Such an action can help protect the system from manipulation, but on the other hand, it can lead to a drop in performance or increased energy expenditure.
Source: Ben Gurien University (Arxiv)
Trending on Canaltech:
- What if a person only eats meat?
- The 10 most viewed films of November 2022
- It appears that the Earth will run out of oxygen faster than we thought
- You will never flush the toilet with the lid open after watching this video
- Twitter starts releasing the gold seal, but the gray is still out
- Top 10 strategy games for Android
🇧🇷The best content in your email for free. Choose your favorite Terra newsletter. Click here!
Source: Terra
Camila Luna is a writer at Gossipify, where she covers the latest movies and television series. With a passion for all things entertainment, Camila brings her unique perspective to her writing and offers readers an inside look at the industry. Camila is a graduate from the University of California, Los Angeles (UCLA) with a degree in English and is also a avid movie watcher.





